AWS Elastic Cloud Compute
Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides resizable computing capacity—literally, servers in Amazon’s data centers—that you use to build and host your software systems.
Instance Types
EC2 instances come with different configurations dedicated to different use cases. You can check out the list of the different configurations on: https://aws.amazon.com/ec2/instance-types/:
- General Purpose
- Compute Optimized
- Memory Optimized
- Accelarated Computing
- Storage Optimized
Naming convention
Instances’ names follow a naming convention with pattern like:
<type><hardware-generation>.<instance-size>For example, the instance type t4g.medium represents:
- Type
twhich is a general purpose instance, - Hardware generation
4gwhich is based on AWS Graviton 2 ARM processor for this specific type, - Instance size
mediumwhich stands for medium memory and CPU ressources, 2vCPU / 4Gio here.
Amazon Machine Image
An AMI is a template that contains the software configuration (Operating System, Application Server and application) required to launch your instance. You can select an AMI provided by AWS, the user community, the AWS Marketplace, or one of your own pre-built AMI.
User data
Script that will be launch at the first boot of the instance and will be run only once.
Security Group
It is fundamental in AWS network security:
- It controls how traffic is allowed into and out of the EC2 instances.
- It only contains ALLOW rules.
So it acts as a firewall in front of the EC2 instance. It filters access to:
- Port number,
- IPv4 and IPv6 range,
- Inbound network traffic (into the instance),
- Outbound network traffic (out of the instance).
That means when traffic is blocked, the EC2 instance won’t even see it:
- If you end up with a time-out issue when accessing your application, it’s probably a Security Group issue.
- If you encounter a connection error, then the traffic went through the Security Group and that’s an application error issue (the application did not launch, for example).
A Security Group can reference rules, but also others Security Groups:
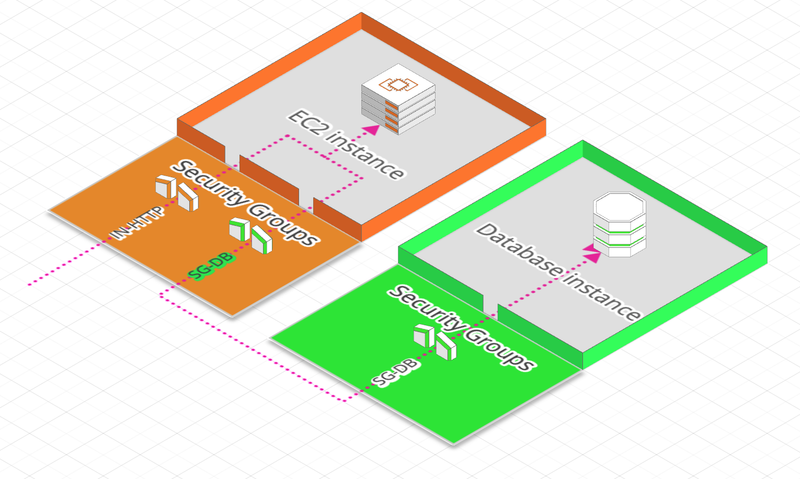
The Security Group SG-DB attached to the Database allow traffic inbound to our EC2 instance because we also have attached the SG-DB Security Group to our EC2 instance.
Instance Purchasing options
AWS offers different kind of purchasing when it comes to instances and some of them can reduce cost:
On-Demand instances:
For short workload, with a predictable price, you pay what you use (no cost saving)Reserved and with a minimum of 1 or 3 years(up to 75% discount):
Reserved instances:
For long workloads (a database for example)Convertible Reserved instances:
Long workloads, but you can change the instance type (from t2-2xlarge to c5-small for example)(up to 54% of discount)Scheduled Reserved instances:
When you don’t need continuously an instance (for example you need an instance every Sunday per week but during one year at least)
Spot instances:
For short workloads with resilience but less reliable as you can lose your instance if the price you’re willing to pay for them is less than the current Spot price (provide the highest discount in AWS that can be up to 90%). Useful for batch jobs, distributed workloads, image processing, …Dedicated Host (for a period of 3 years):
Reserves an entire physical server fully dedicated to your use in AWS datacenter. When you have compliance requirements or use a Bring Your Own License model (BYOL)




